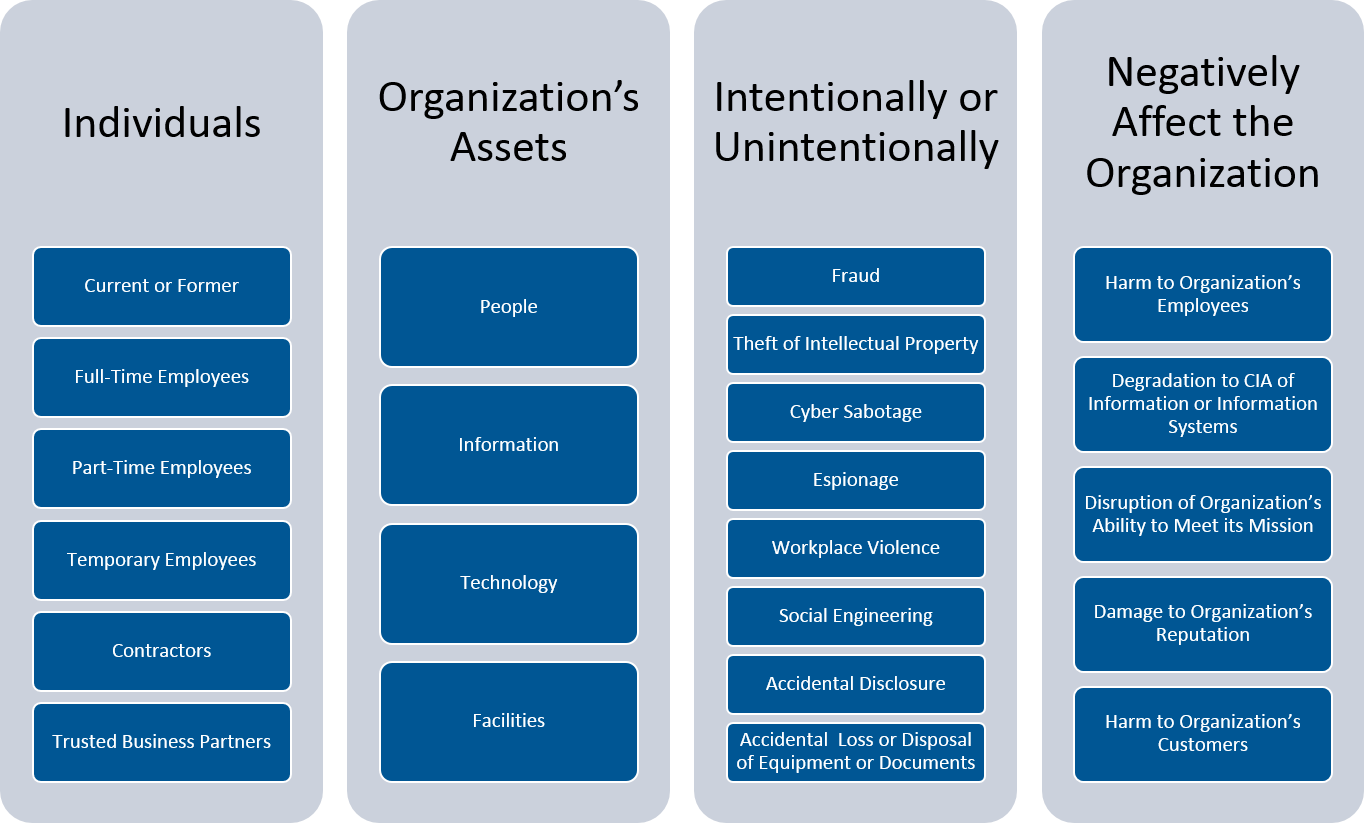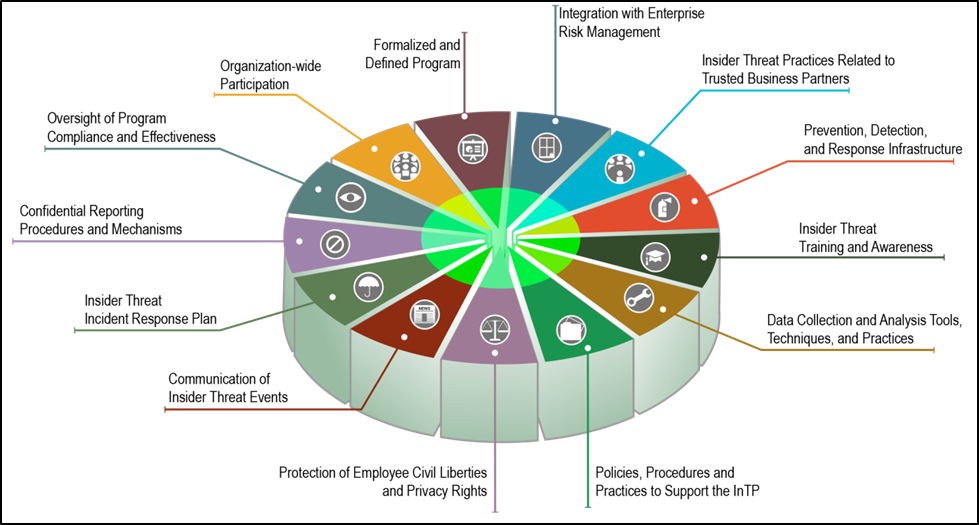
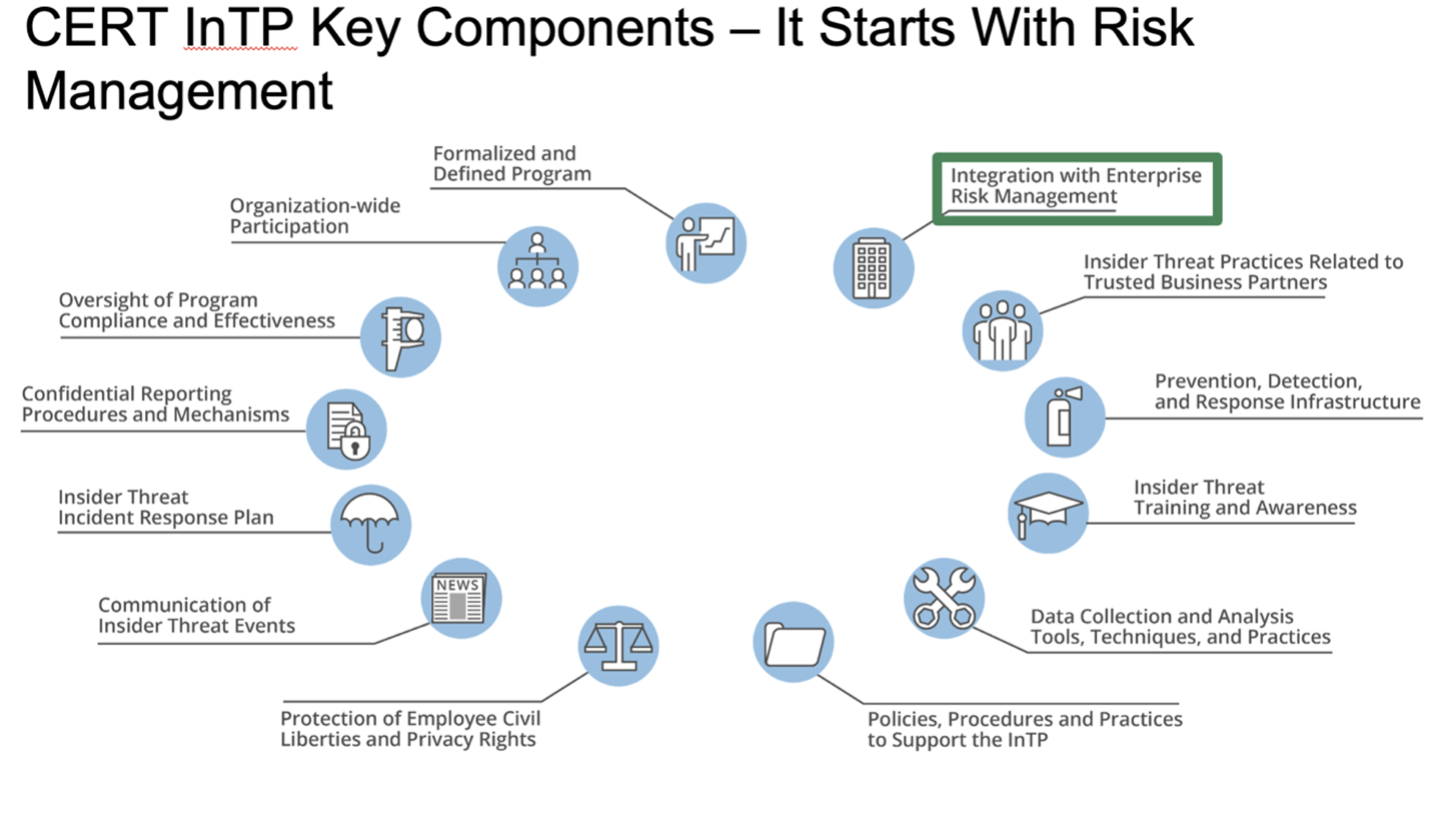
Formalized Insider Threat Program (Part 2 of 20: CERT Best Practices to Mitigate Insider Threats Series)

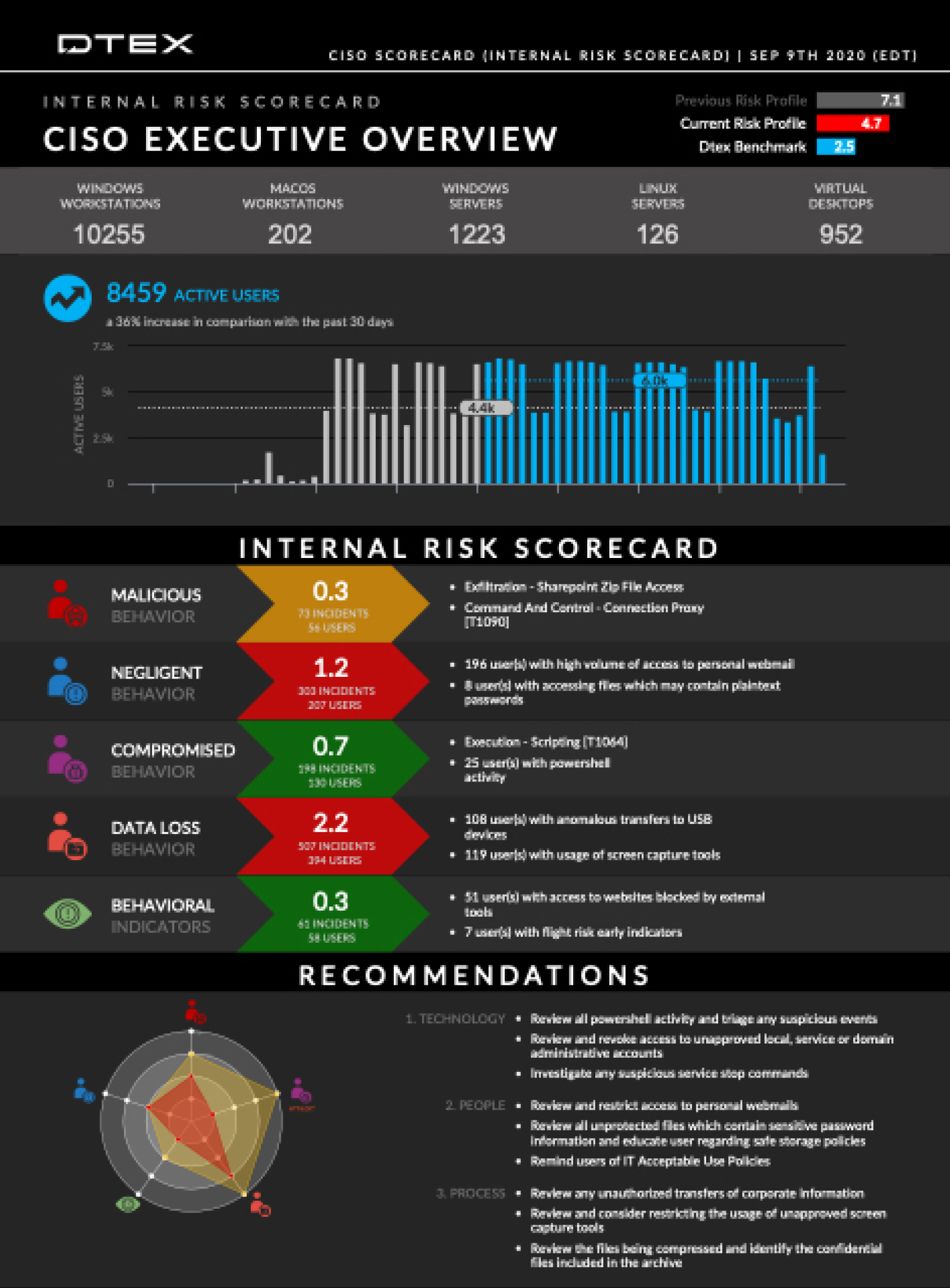
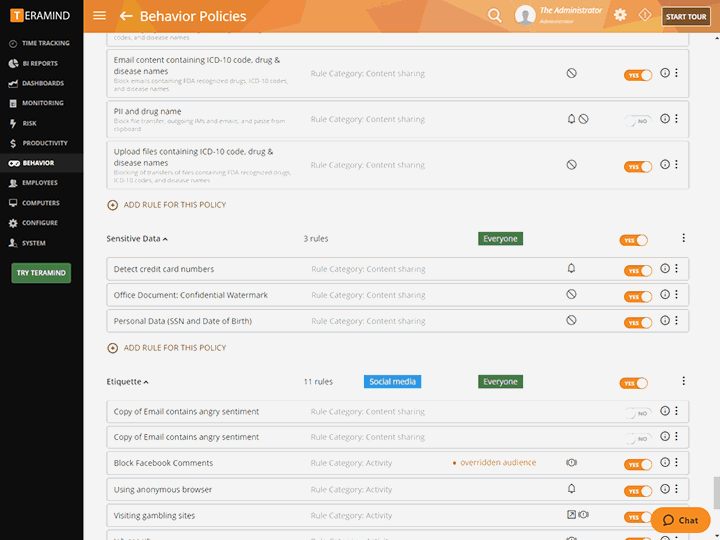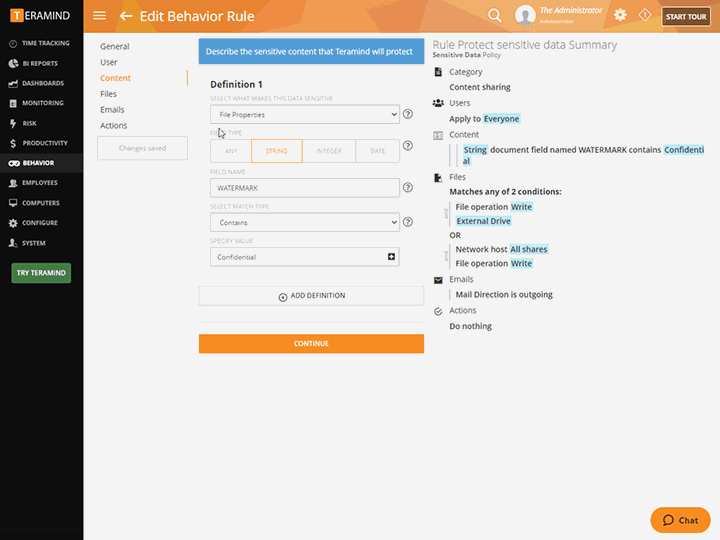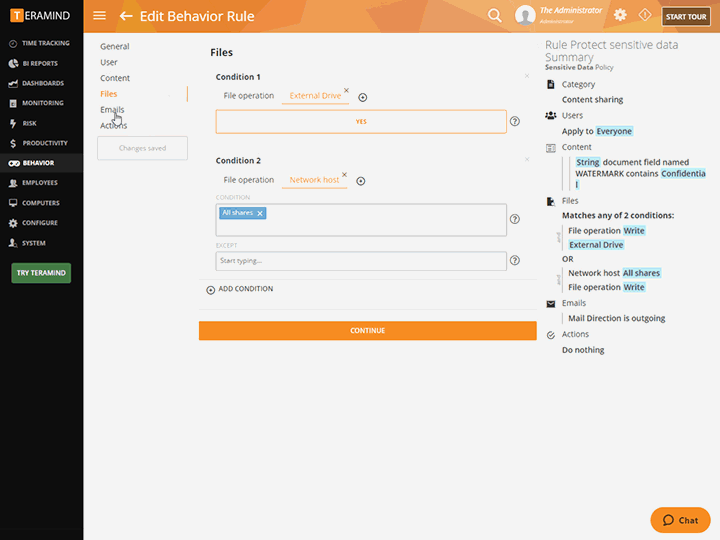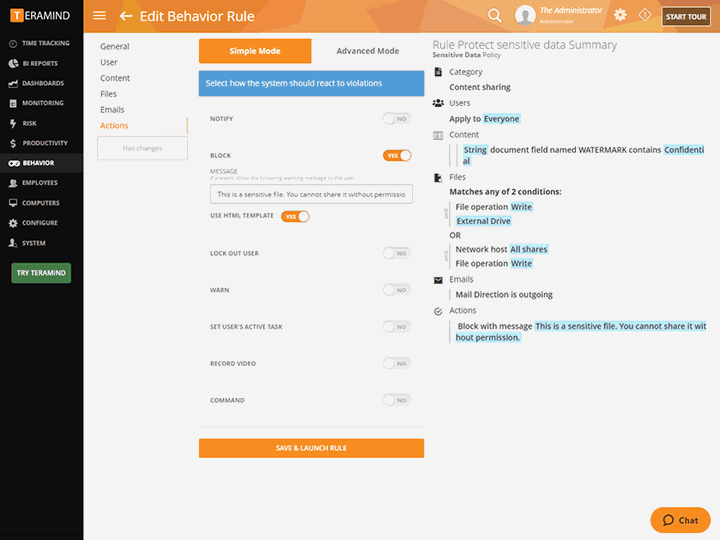
Insider Threat Program: give yourself the tools to spot and address threats faster and more effectively

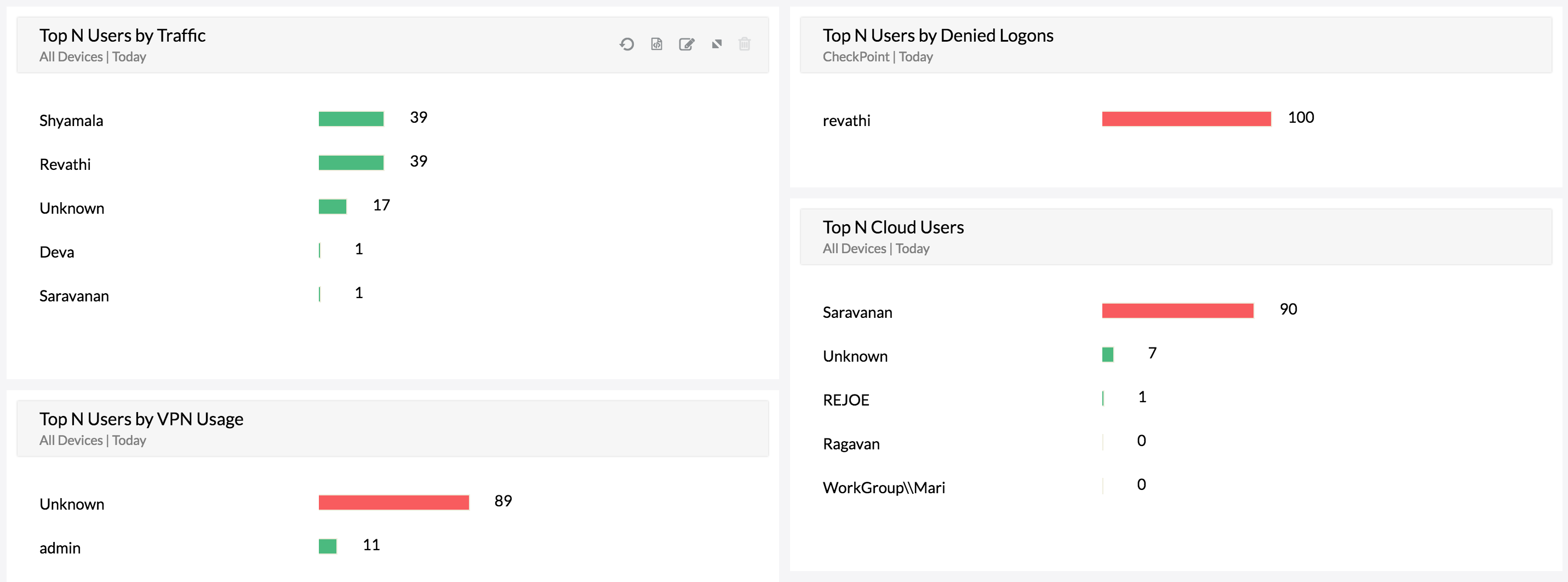
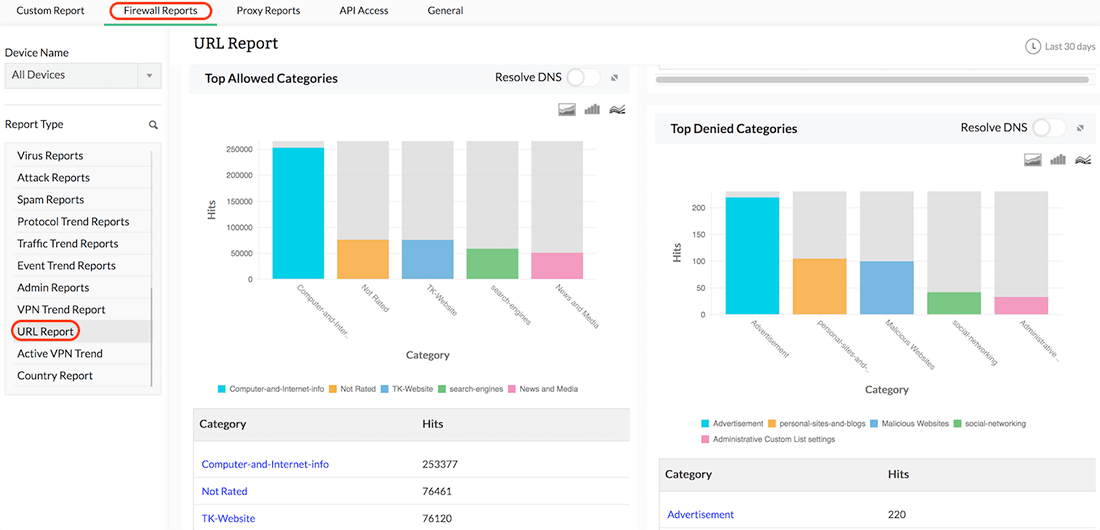
Insider Threats Risk Assessment | Insider Threats Security Audit | Protect Insiders - SaaS Security Posture Management

![Building an Insider Threat Program [10-step Checklist] | Ekran System Building an Insider Threat Program [10-step Checklist] | Ekran System](https://ekran_site_uploads.storage.googleapis.com/wp-content/uploads/2023/09/12225318/pic-3-How-to-Build-an-Insider-Threat-Program-10-step-Checklist.png)






![Building an Insider Threat Program [10-step Checklist] | Ekran System Building an Insider Threat Program [10-step Checklist] | Ekran System](https://ekran_site_uploads.storage.googleapis.com/wp-content/uploads/2023/09/12232127/pic-7-How-to-Build-an-Insider-Threat-Program-10-step-Checklist.png)