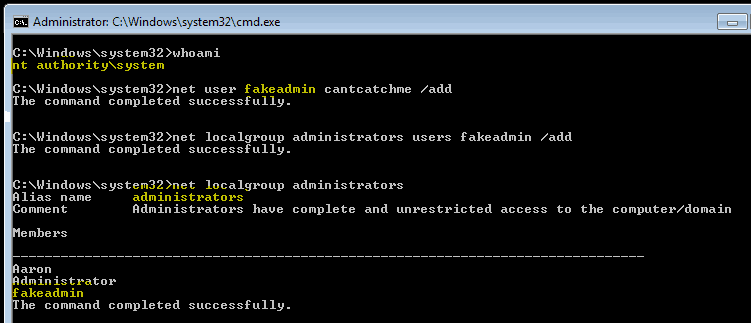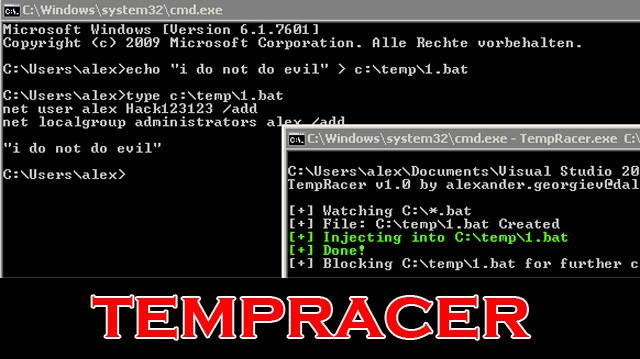
TempRacer - Windows Privilege Escalation Tool - Darknet - Hacking Tools, Hacker News & Cyber Security
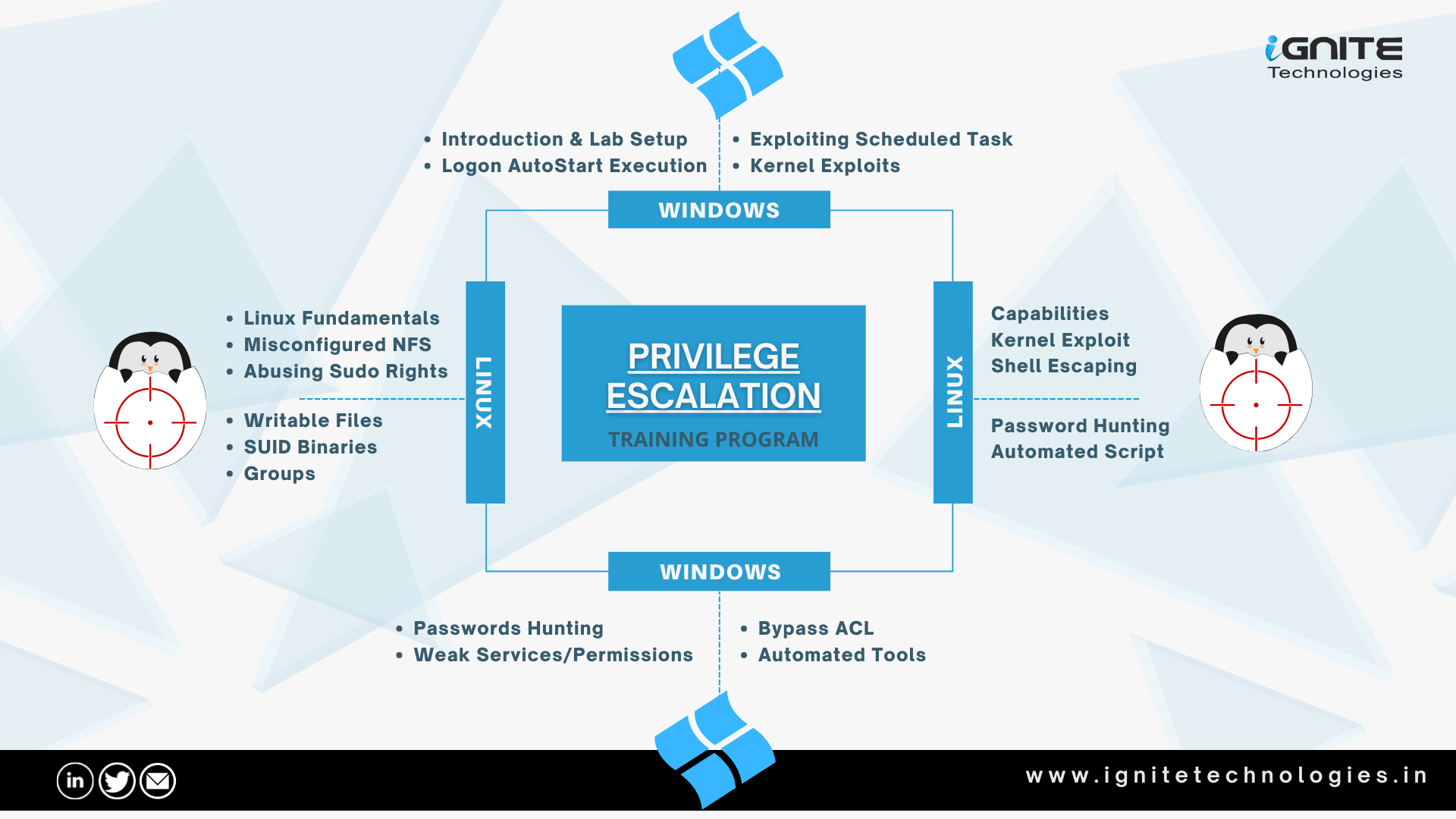
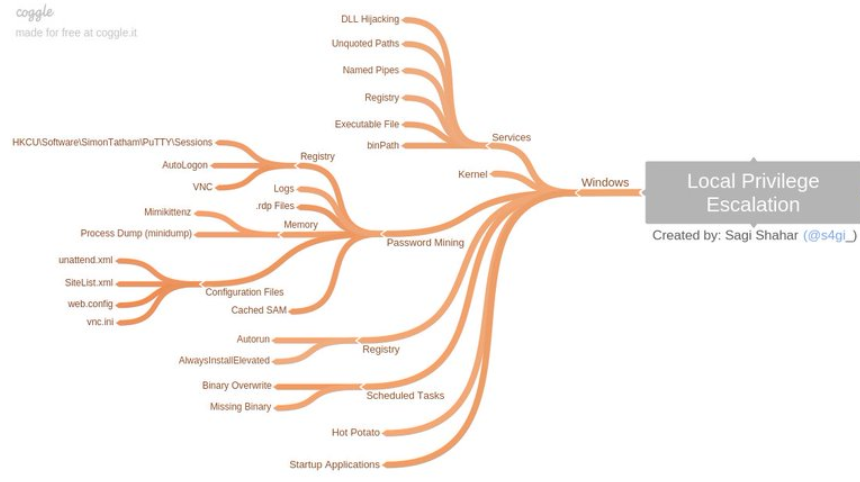
GitHub - Ignitetechnologies/Linux-Privilege-Escalation: This cheatsheet is aimed at the OSCP aspirants to help them understand the various methods of Escalating Privilege on Linux based Machines and CTFs with examples.

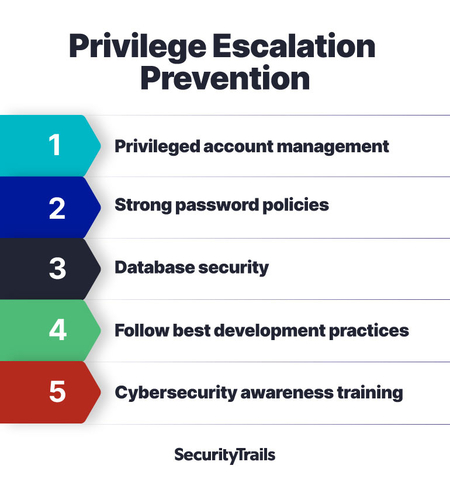
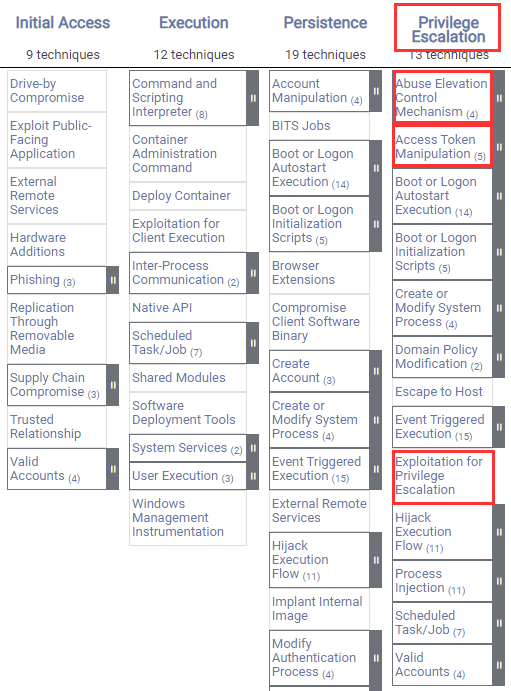
What Is A Privilege Escalation Attack? How To Prevent Privilege Escalation Attacks? - The Sec Master

TryHackMe — Jr Penetration Tester | Privilege Escalation | Linux Privesc | Part 2 | by Aditya Sharma | Medium

Offensive Security Tool: PEASS (Privilege Escalation Awesome Scripts Suite) As Shell is the beginning, once a hacker accesses a system, which is not so... | By Black Hat Ethical HackingFacebook


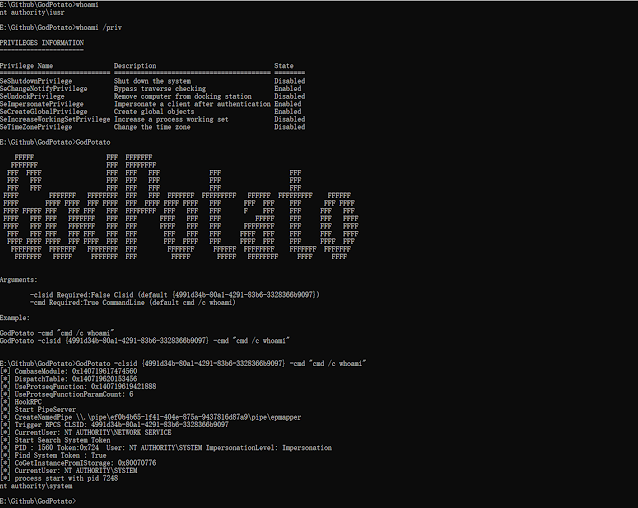


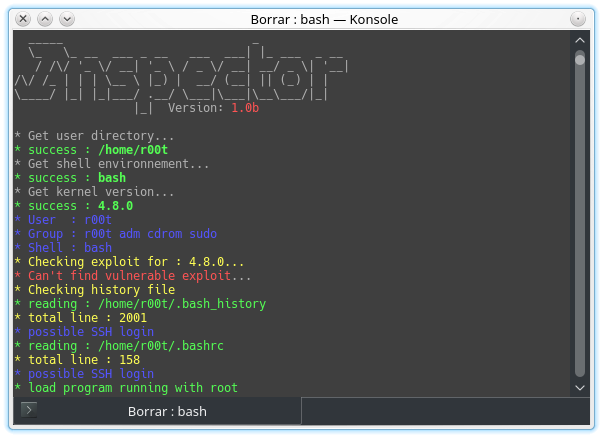



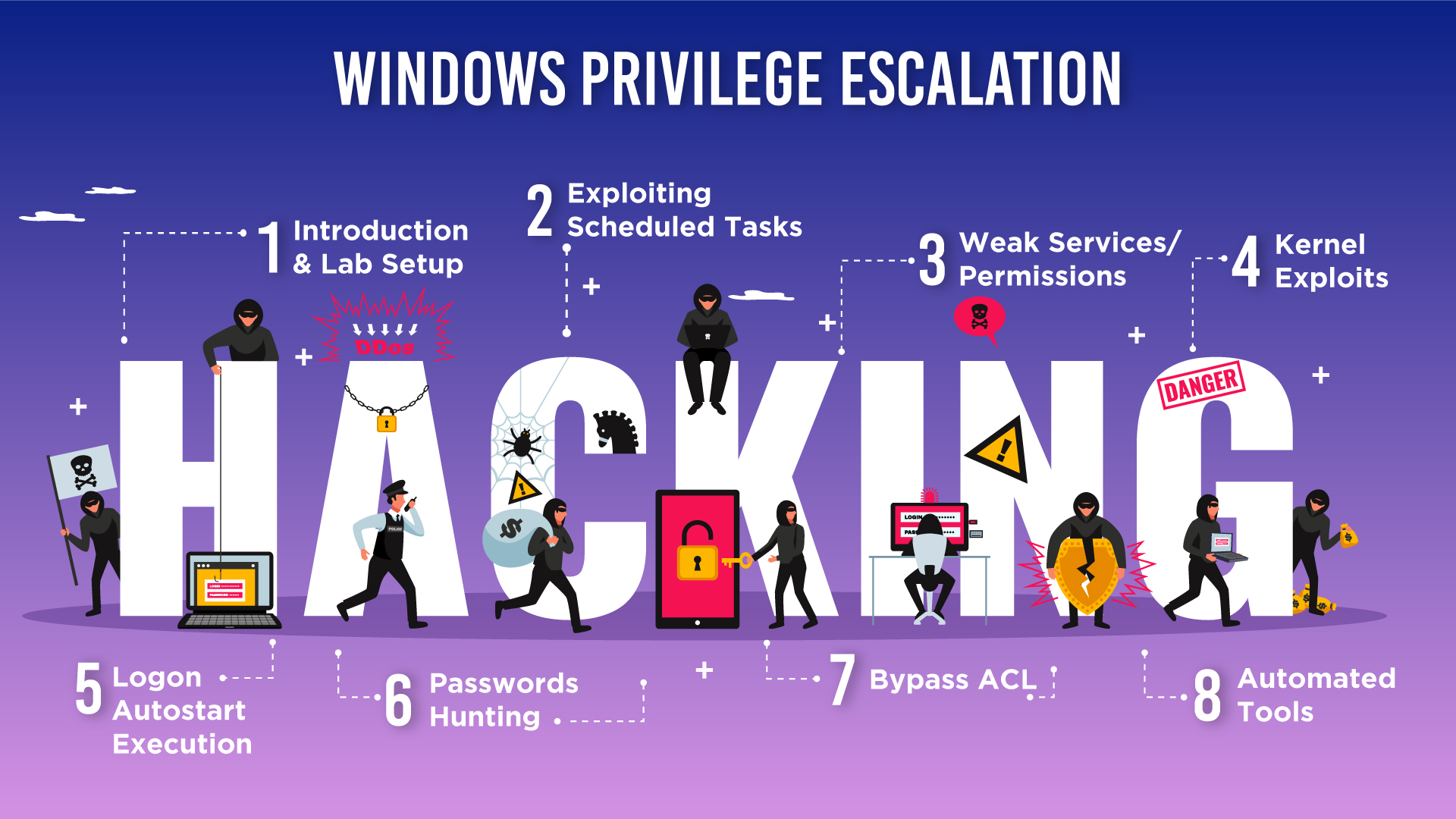
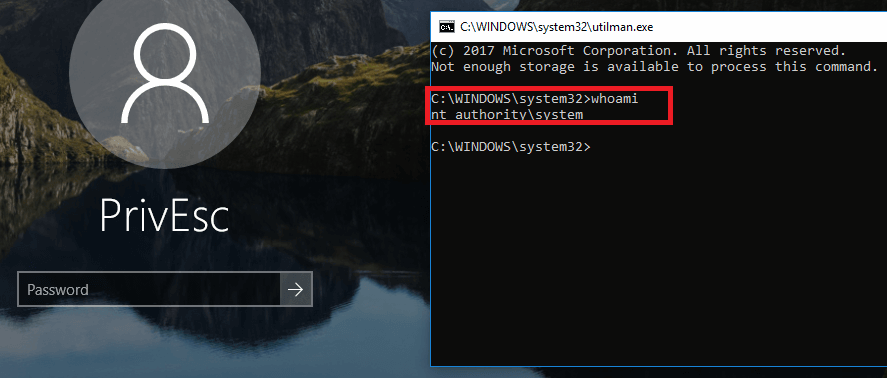


![Privilege Escalation with PowerShell Empire and SETOOLKIT [Kali Linux] - Yeah Hub Privilege Escalation with PowerShell Empire and SETOOLKIT [Kali Linux] - Yeah Hub](https://www.yeahhub.com/wp-content/uploads/2018/08/powershell-empire-priv-esc-setoolkit-2.png)