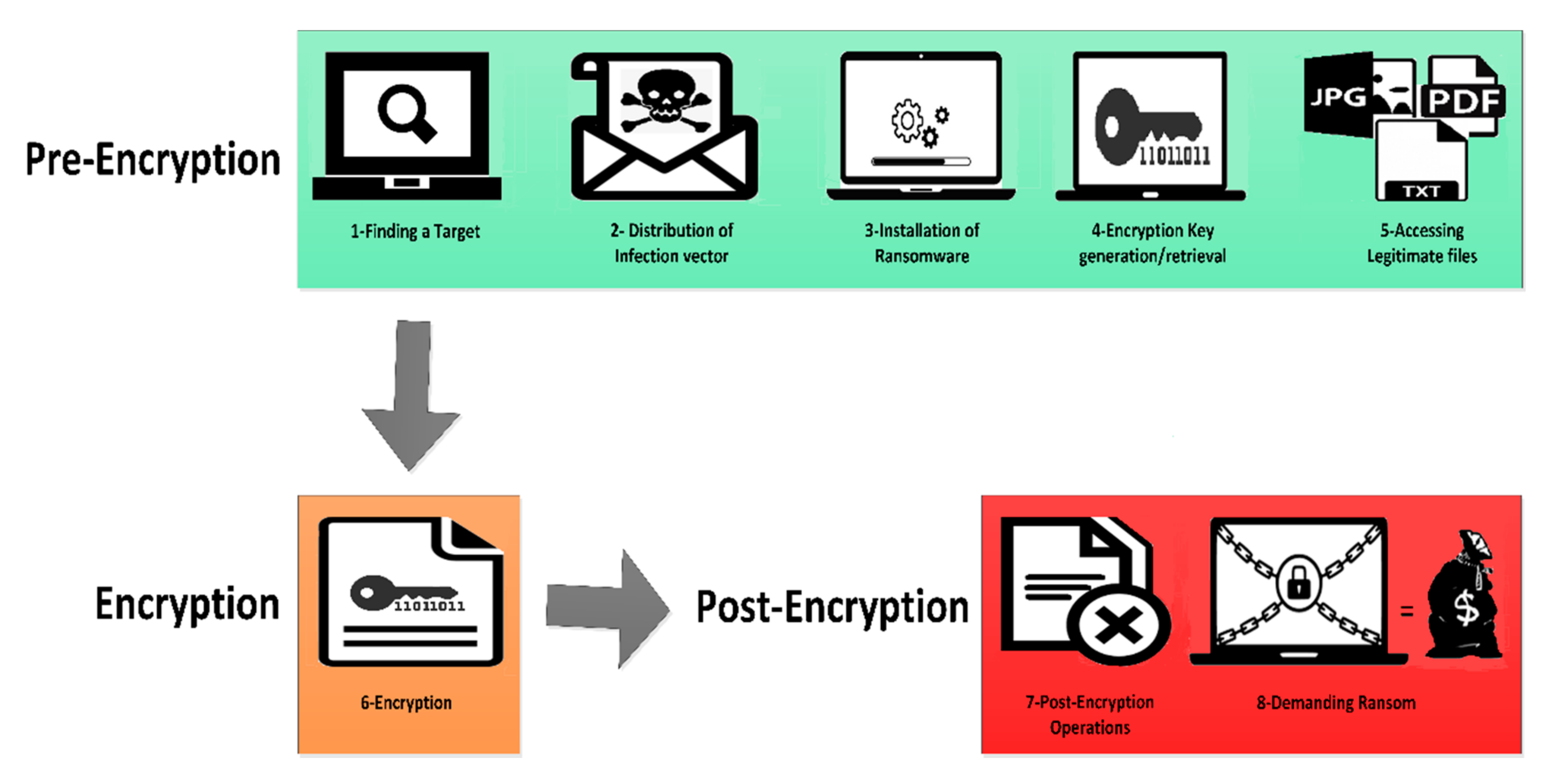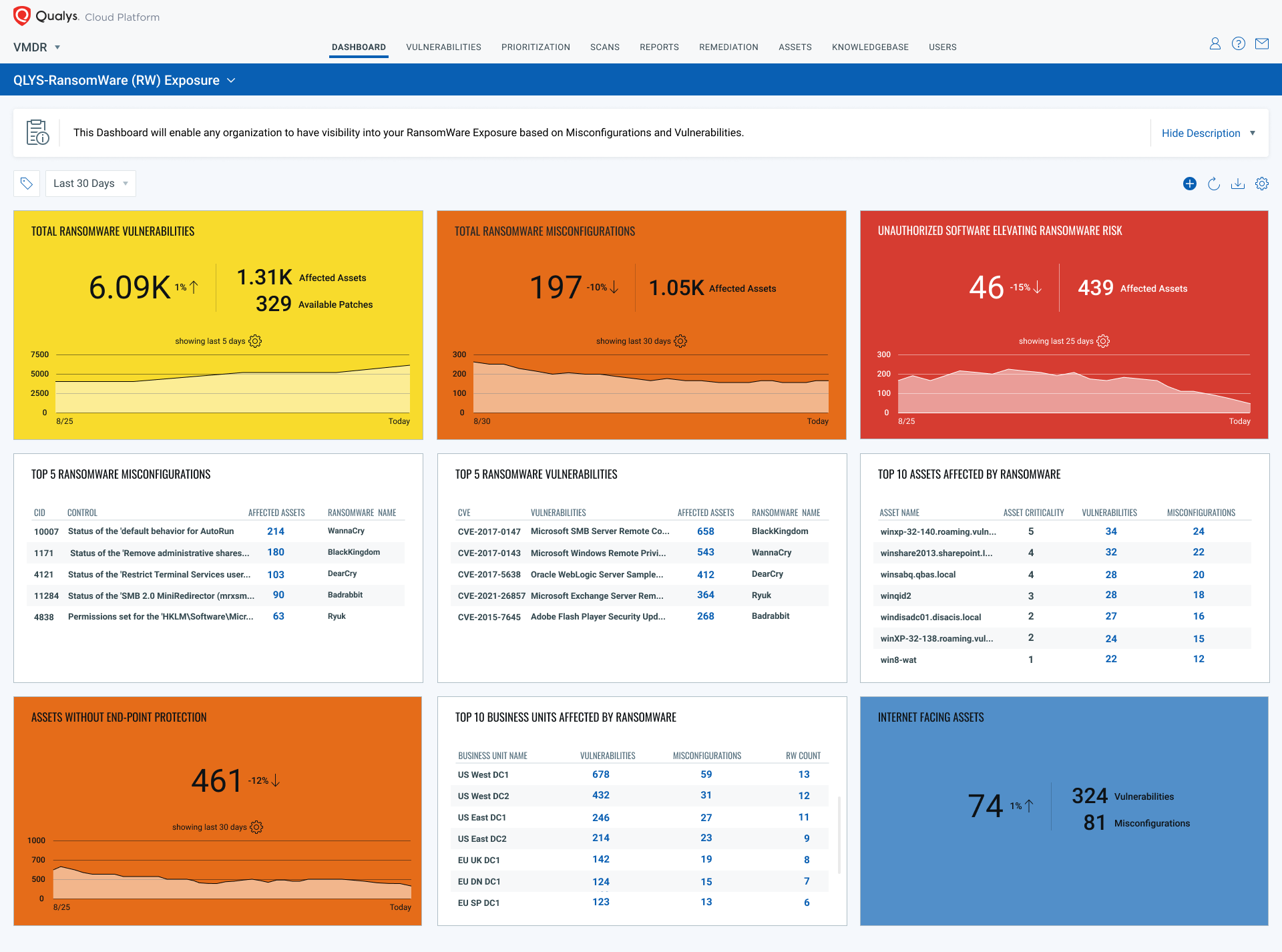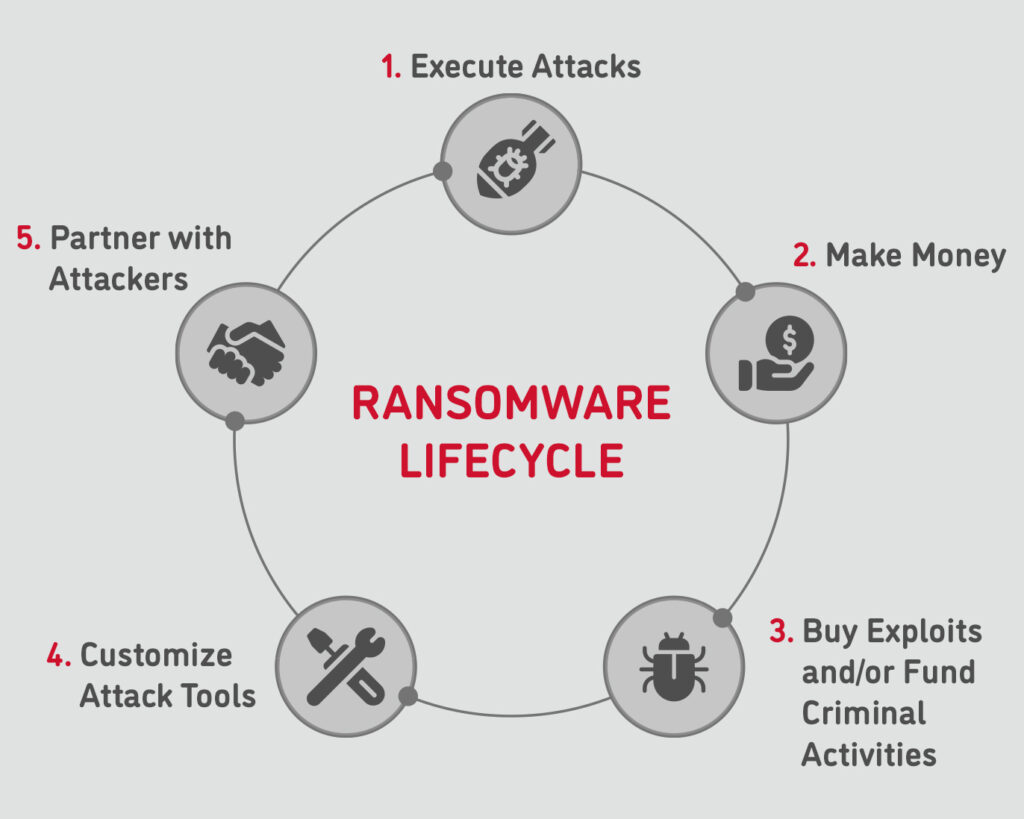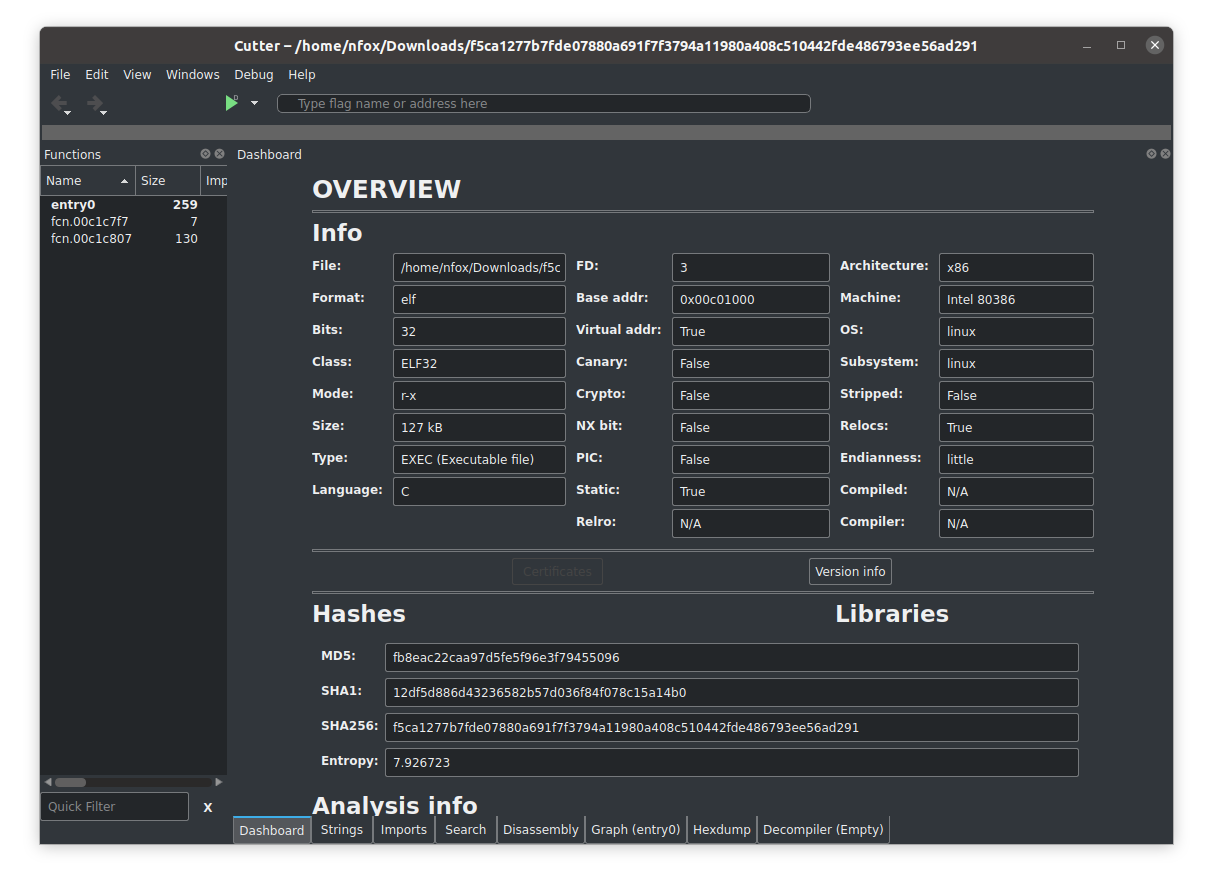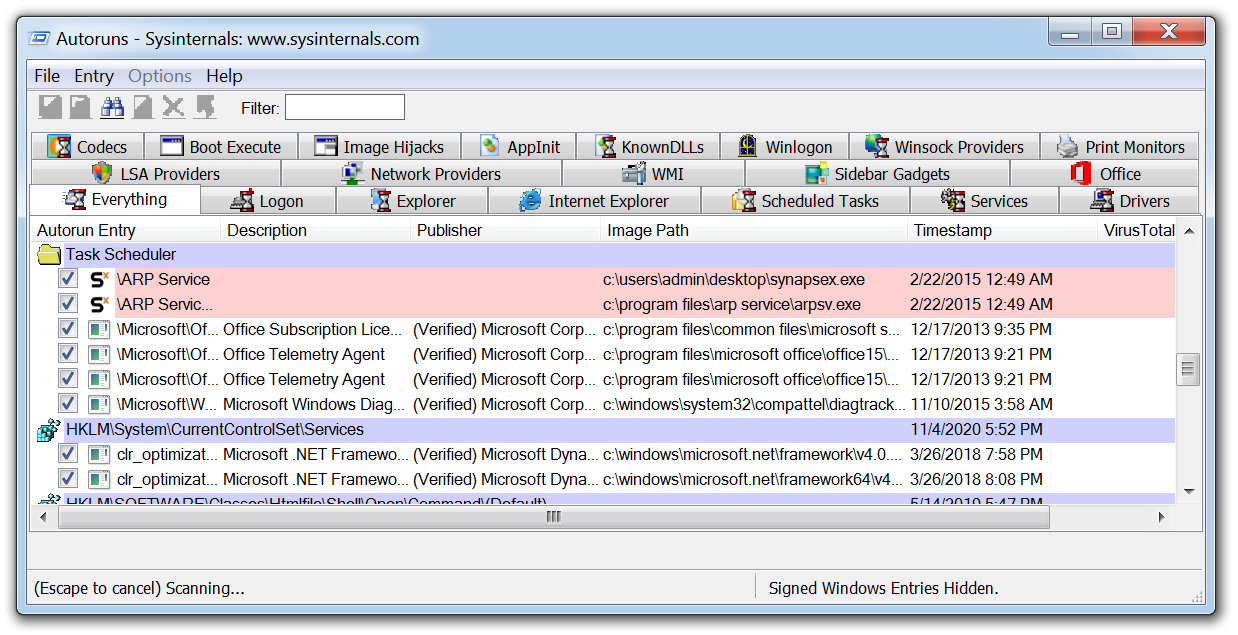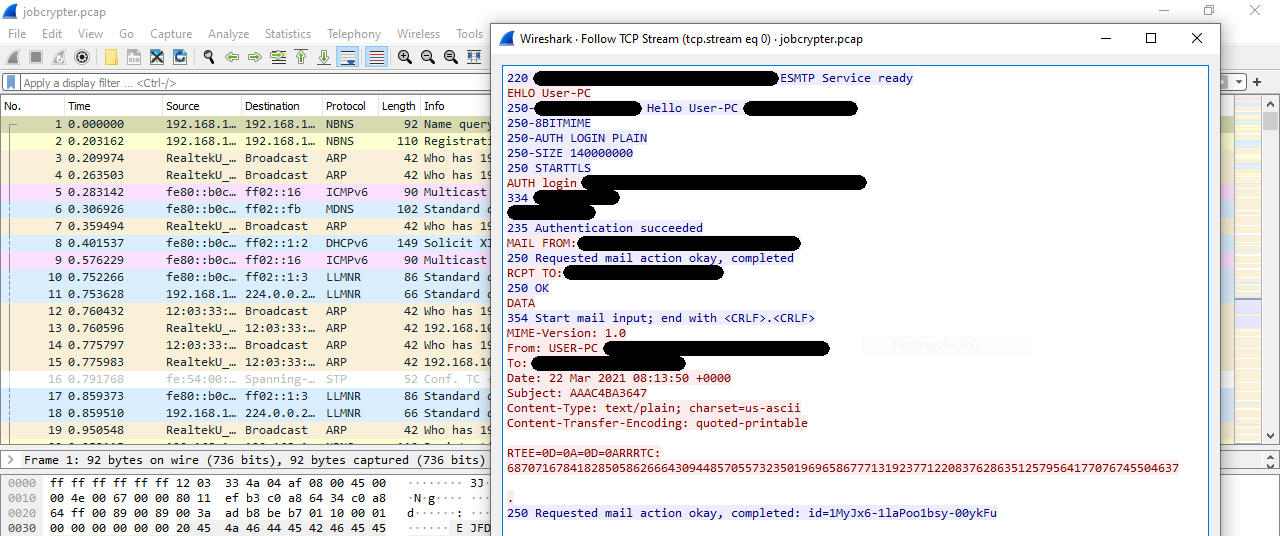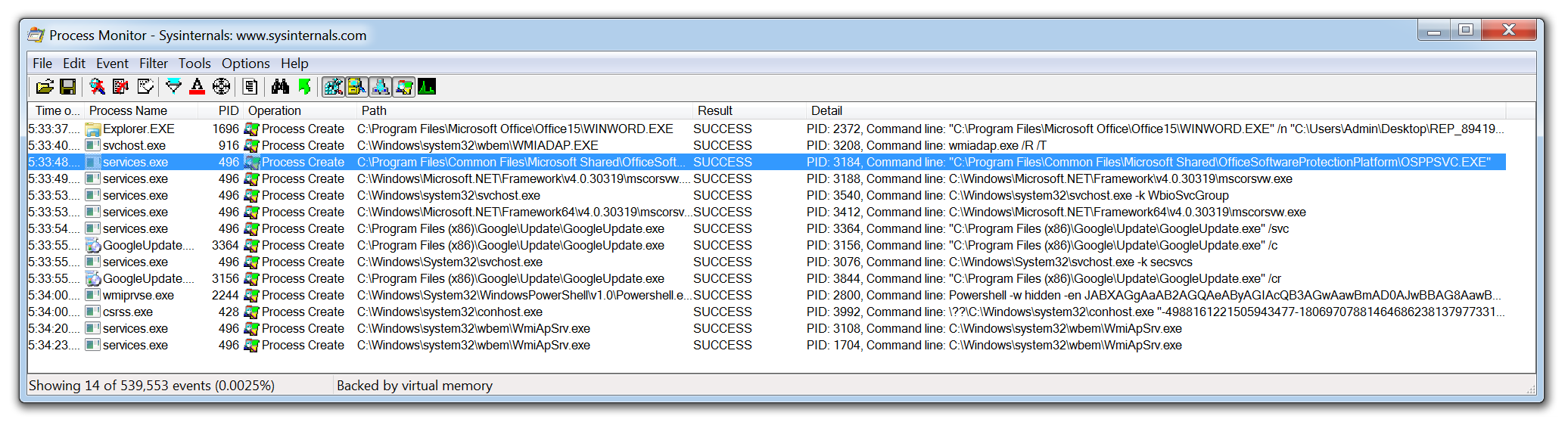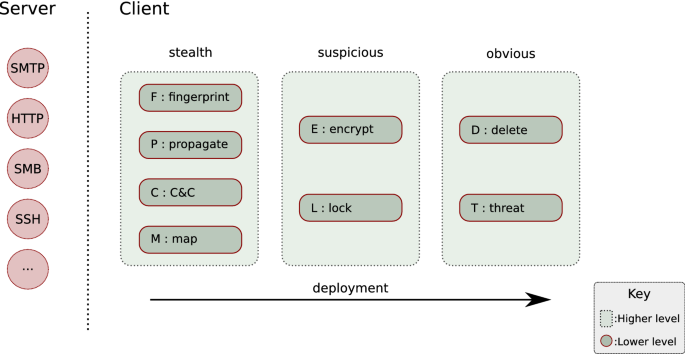
Ransomware deployment methods and analysis: views from a predictive model and human responses | Crime Science | Full Text
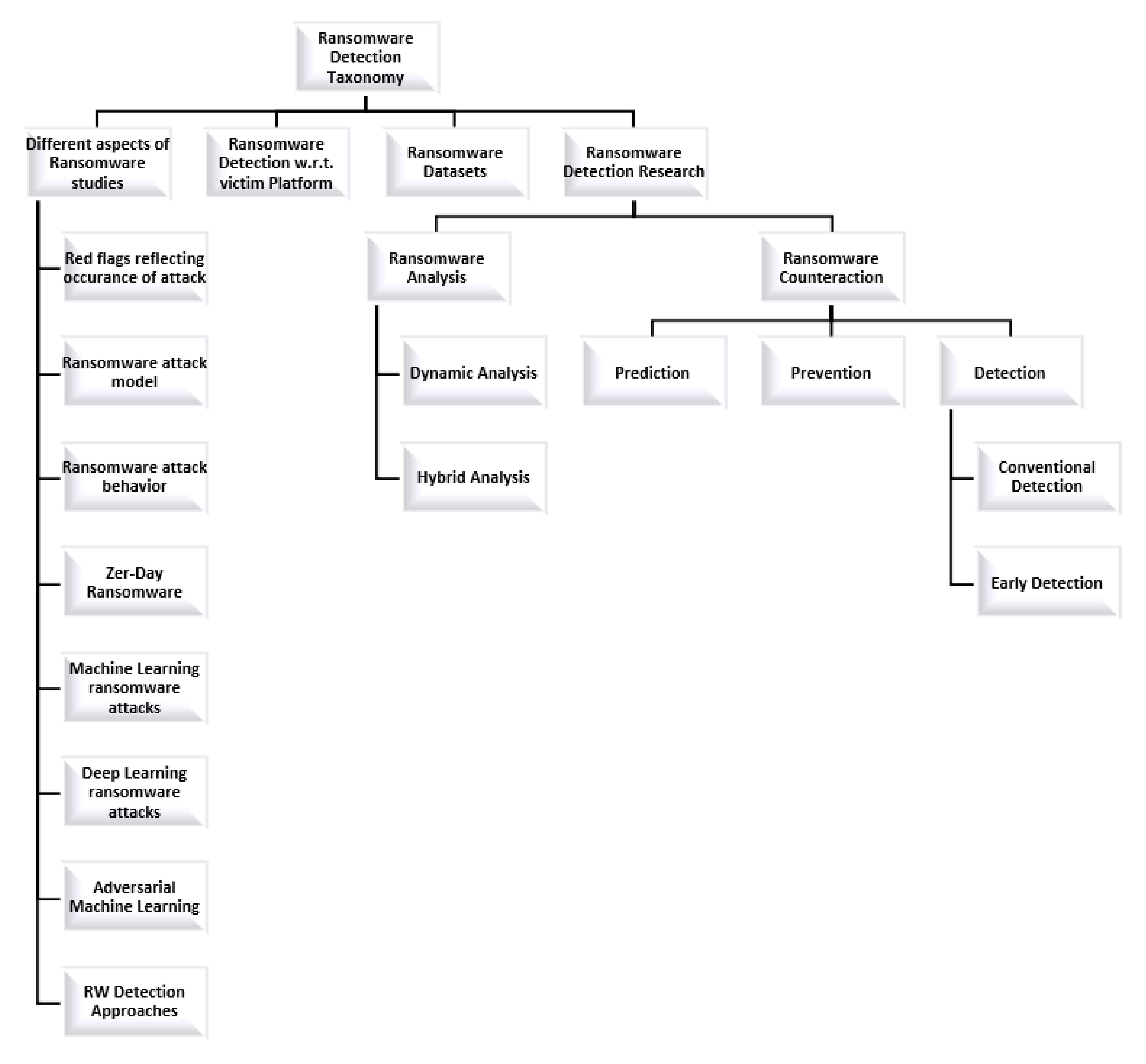
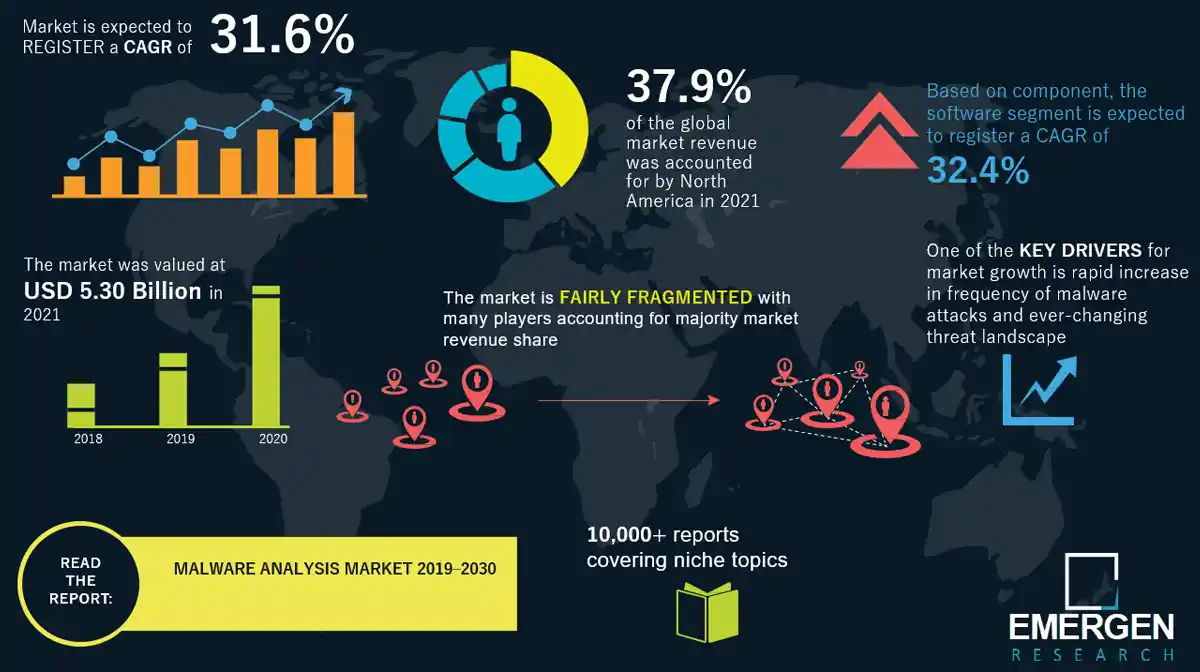
Applied Sciences | Free Full-Text | Ransomware Detection Using the Dynamic Analysis and Machine Learning: A Survey and Research Directions