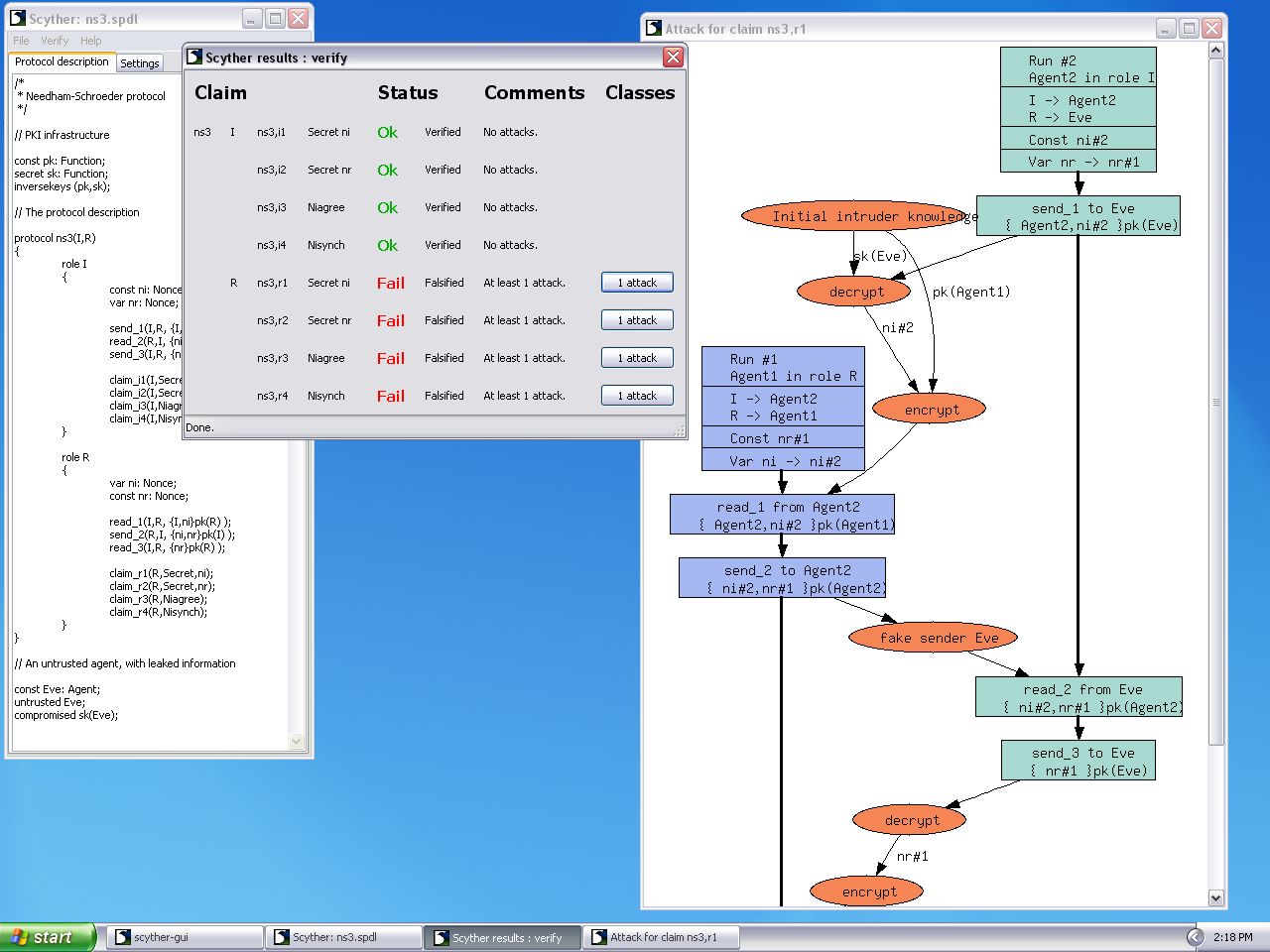
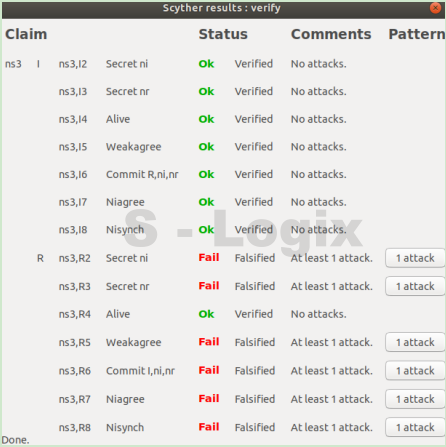
A privacy-preserving handover authentication protocol for a group of MTC devices in 5G networks - ScienceDirect
GitHub - binhnguyen1984/scyther-abstraction: The Scyther-abstraction Tool for the symbolic analysis of security protocols
![PDF] Analysis and Verification of a Key Agreement Protocol over Cloud Computing Using Scyther Tool | Semantic Scholar PDF] Analysis and Verification of a Key Agreement Protocol over Cloud Computing Using Scyther Tool | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/df932f9db948e0e49c26a748ca2eec9d76e3c118/5-Figure3-1.png)
PDF] Analysis and Verification of a Key Agreement Protocol over Cloud Computing Using Scyther Tool | Semantic Scholar

Simulation results of the Scyther tool. Figure includes two pictures.... | Download Scientific Diagram

An efficient authentication and key agreement protocol for IoT-enabled devices in distributed cloud computing architecture | EURASIP Journal on Wireless Communications and Networking | Full Text
A Strong Mutual Authentication Protocol for Securing Wearable Smart Textile Applications. - Document - Gale Academic OneFile